To ensure database security, implement robust encryption and access controls. Regular backups are vital for data recovery in case of a breach or failure.
Databases store crucial information and are essential to most businesses. They hold around 120 words of well-rounded data. Safeguarding this data is a top priority for any organization. They want to protect it from unauthorized access, corruption, or loss.
Effective security measures are fundamental. They include advanced encryption techniques and rigorous access control systems. They protect sensitive information from potential threats.
Similarly, consistent backup strategies are indispensable. They maintain data integrity. They also provide a safety net for quick restoration following unexpected incidents. Data breaches are becoming more sophisticated.
Organizations must proactively update and refine their security protocols. Ensuring a resilient backup schedule complements these efforts. It provides assurance that critical data can be retrieved. Operations can continue with minimal disruption.

Credit: www.redswitches.com
Essential Database Security Measures
Keeping databases secure is crucial for businesses today. Data breaches can lead to serious consequences. Protecting sensitive information requires robust security measures. The following strategies are key to safeguarding your database assets.
Encryption: The First Line Of Defense
Encryption acts as a powerful barrier. It scrambles data, making it unreadable without a key. Implementing strong encryption standards shields data effectively. Encrypt data both at-rest and in-transit. Use industry-proven encryption algorithms. Regularly update encryption keys for enhanced security.
Regular Security Audits And Vulnerability Assessments
Regular checks keep security tight. Conduct security audits to spot potential weaknesses. Partner with security experts for unbiased assessments. Utilize automated tools for ongoing vulnerability scans. Align with best practices and compliance requirements. Fix issues promptly to maintain a rigid defense.
| Action | Purpose |
|---|---|
| Implement Encryption | Secure data from unauthorized access |
| Audits | Identify and remedy security gaps |
| Regular Updates | Ensure protection against new threats |
- Use firewalls to block malicious traffic.
- Restrict access to essential personnel only.
- Apply multi-factor authentication for user logins.
- Review and update access controls periodically.
- Stay informed on latest security trends and threats.
- Test backup systems to ensure data recovery is possible.
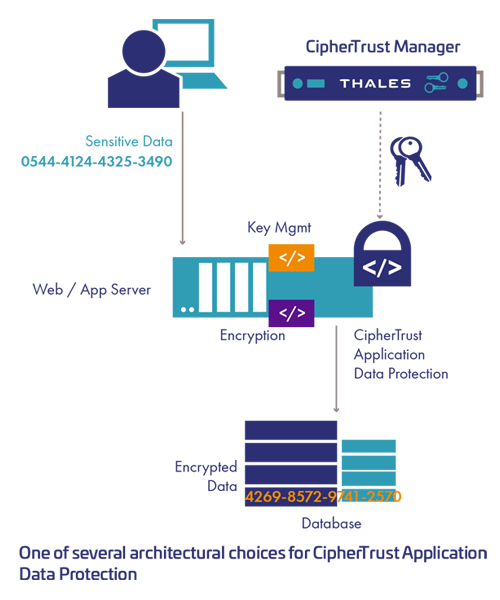
Credit: cpl.thalesgroup.com
Access Control Strategies
Your database is the heart of your digital presence. Keeping it secure is a top priority. Smart access control strategies are critical. They help ensure only the right eyes see your data. Let’s dive into how you can reinforce your database’s defenses.
Implementing Role-based Access
Role-Based Access Control (RBAC) limits access to your database. It does so by assigning roles to users. Each role has specific permissions. This method organizes access by job function. Users only get the access they need to do their work.
- Create roles like Admin, Editor, and Viewer.
- Assign permissions to each role. For example, allow Admins full access.
- Grant access based on user roles, not individual needs.
Multifactor Authentication For Sensitive Operations
Extra layers of security matter. Multifactor Authentication (MFA) adds these layers. It requires more than one piece of evidence to login. Think of it as needing multiple keys to open a treasure chest. It’s a smart way to protect sensitive operations.
- Enable MFA where critical data is involved.
- User logins must pass through at least two checks.
- Combos can include passwords, codes, or biometrics.
Backup And Recovery Plans
A robust Backup and Recovery Plan is essential. It’s a pillar for maintaining database integrity and availability. Without it, data loss can cause irreparable damage. It can harm an organization’s operations and reputation. These plans secure data against a variety of threats. The threats include hardware failures, software bugs, and human error.
Backup and Recovery Plans
Scheduled Backups: A Safety Net Approach
Scheduled Backups: A Safety Net Approach
Scheduled backups act as a safety net for any organization’s data strategy. Like clockwork, they capture snapshots of vital information, ensuring that recent data changes are not lost.
| Backup Frequency | Benefits |
|---|---|
| Daily | Minimizes data loss in daily operations |
| Weekly | Protects against more significant incidents |
| Monthly | Provides a long-term data safety net |
Testing Recovery Procedures: The Unsung Hero
Testing Recovery Procedures: The Unsung Hero
Regular testing of recovery procedures is critical. It’s the shield that guards the realm of data. Untested backups can fail when needed the most, compounding a disaster rather than resolving it.
- Mock Disaster Scenarios: Practice restores to prepare for real threats.
- Recovery Time Objectives: Ensure rapid response capabilities.
- Audit Recovery Results: Confirm successful data restoration and integrity.
Tackling Threats: Proactive Measures
Every day, databases face countless threats. Data breaches and attacks can cripple any business. It is essential to stay ahead of these threats. Proactive security measures are not just important. They are mandatory in today’s digital landscape. Let’s dive into effective strategies to protect your database assets.
Real-time Monitoring And Alerts
Real-time monitoring is like having a security guard for your digital data. It helps track every access and change. With it, you get alerts for suspicious activities at once. This means you can stop threats before they cause harm. Below are steps to set up an efficient real-time monitoring system:
- Install Security Software: Choose a solution that specializes in database protection.
- Configure Alerts: Set up notifications for unusual patterns or behavior.
- Regularly Update Settings: Adapt to new threats by updating alert triggers.
- Review Logs: Frequently analyze logs to detect and address vulnerabilities quickly.
Anticipating Sql Injections And Cross-site Attacks
SQL injections and cross-site attacks are common yet dangerous. They can give attackers access to your database. Beat these threats with robust defenses laid out ahead:
- Use Prepared Statements: This coding practice keeps database queries secure.
- Sanitize User Input: Always check data from users to prevent malicious code entry.
- Apply Web Application Firewall: A firewall adds a layer of protection against unwanted traffic.
- Regular Patching: Keep your database and applications updated to close security gaps.
Stick to these steps, and you give your databases a fighting chance against online threats. Remember, security is ongoing. Always be vigilant.
Legal And Compliance Considerations
Keeping databases secure is critical, not only for business integrity but also to meet legal requirements. Laws dictate how data should be handled. This ensures that personal information is safe.
Navigating Data Protection Regulations
Understanding global data protection laws is essential. The rules vary by country. They dictate how data must be treated. Compliance protects companies from penalties.
Key regulations include GDPR in Europe and CCPA in California. Both focus on protecting people’s data. Compliance ensures customer confidence and legal safety.
Audit Trails And Compliance Reporting
Audit trails are vital. They track database activities. These logs are proof of compliance. They help during external audits.
- They show who accessed data and when.
- They reveal changes made to the database.
- They are required by many laws.
Reports from these trails must be clear. They should be easy to understand. Accurate reports show regulators that a company is serious about data security.

Credit: delinea.com
Frequently Asked Questions for Ensuring Security and Backups for Databases?
How Do You Ensure Security In A Database?
Ensure database security by implementing strong password policies and regular updates. Use encryption for sensitive data and apply access controls. Regularly back up the database and monitor for unusual activity. Keep security software and patches current.
How Can You Ensure Backups Are Secure?
Ensure secure backups by using strong encryption. Implement access controls and regularly update security protocols. Perform backup integrity checks and choose reputable storage solutions.
What Is Database Security Backup?
A database security backup involves creating copies of your data. This prevents loss from system failures or cyberattacks. This safeguarding practice ensures data recovery for business continuity.
How To Ensure Security Of Data Network Access And Backup Systems?
Implement strong passwords and regularly update them. Use multi-factor authentication for added security. Regularly back up data on secure, encrypted servers. Conduct frequent security audits and updates. Train employees on best security practices and protocols.
Conclusion
Securing databases is paramount in safeguarding critical data. Regular backups are your safety net against data loss. Implement robust security measures and frequent backup practices. This will ensure data integrity and availability. Take action now to protect your digital assets. The stability and reliability of your data may depend on it.









